Archive - 19th IFIP Summer School on Privacy and Identity Management 2024

Proceedings
The proceedings have been published by Springer and can be accessed here.
Call For Papers
Generating Futures
Generative AI as a commodity might still be considered a novelty, but it is already significantly impacting society. Its ultimate consequences are yet to be discovered, but the immediate effects are already visible, especially in combination with other technologies: from assistants linked to e-commerce platforms to home control systems, all the way to our workplace, especially in creative industries, there seem to be many possible applications.
At the same time, in several instances, outcomes of AI systems have already led to harm, such as discrimination or fake news. If we do not want the providers of AI systems to generate our future on their own, we will need a broad societal effort to decide how to deal with this technology. Policymakers and data protection authorities have already clarified that, e.g., before using generative AI, it must comply with privacy and data protection rules. Identity management, security, and confidentiality are also pivotal for developing safe AI.
The 19th IFIP Summer School on Privacy and Identity Management welcomes contributions dealing with all privacy and identity management-related research. Nonetheless, this year, we emphasize the interplay between novel AI applications—with a focus on generative AI—and privacy and identity management.
The advent of generative AI technologies has led to many privacy concerns and ethical dilemmas, highlighted by recent high-profile cases, as, quite often, providers of AI services operate globally while disregarding local privacy regulations and ethical considerations. Key issues of these services include using personal data, initially collected for other purposes, to train machine-learning models, and the indiscriminate web scraping by AI tools, potentially capturing personal data in violation of data protection rules, e.g., without consent. A particularly concerning aspect is the unintentional leakage of the personal data used in the training phase by these AI models, such as replicating a training subject’s face with a synthetic face generation tool. Another critical issue is the transparency regarding the fate of data input into AI tools (‘prompts’), often leading to unauthorized use or enhancement of subsequent AI tool versions, affecting the personal data entered in those queries.
Moreover, the tendency of generative AI to produce false or ‘hallucinated’ information, especially when it relates to individuals, poses a significant threat to the data integrity and accuracy principle. The ease of creating fake photo and video montages, such as ‘deep fakes’, through generative AI tools, further exacerbates privacy concerns.
The models underlying generative AI systems often contain racist and sexist material from the open web. Especially when used for decision-making processes, there are serious risks of discrimination and other harms for those affected by those decisions, particularly already marginalized people. These are exacerbated when automated decisions are involved. Current models also lack any explainability and disregard algorithmic transparency principles. Even the software development process is not immune, with tools like Copilot influencing the privacy features of products developed, raising questions about the adherence to privacy concerns and best practices in code generation.
While many of these issues predate generative AI, they are significantly amplified by its emergence. Generative AI products and services must conform to principles such as fairness, accountability, transparency, security, relevance, and non-discrimination to respect and enhance the privacy of the data subjects involved. Our goal is to foster a comprehensive understanding of the challenges and opportunities presented by the intersection of AI and privacy and to explore innovative solutions for the future that respect the rights of those concerned.
The 19th IFIP Summer School on Privacy and Identity Management aims to create a platform for spreading awareness and facilitating interactions and knowledge exchanges around old and new issues by taking a holistic approach to society and technology. We support interdisciplinary research exchange and foster discussions through keynote lectures, tutorials, and workshops. Participants will benefit from presenting their research and receiving meaningful feedback. The IFIP Summer School culminates in the publication of selected papers by the participants as an edited volume published by Springer.
We welcome contributions addressing these issues from any of the following perspectives (and especially the interdisciplinary combination of more than one): sociological, legal, technical, ethical, political, surveillance, intersectional, anthropological, economic, historical, media & communication, regulatory, philosophical, critical, disabilities, and psychological studies in the areas of privacy, data protection, and identity management.
The IFIP Summer School encourages not only interdisciplinarity but also broader diversity. It particularly welcomes submissions on how to foster gender and cultural balance in privacy and identity research and policy, and notably, tutorials and workshops about how to raise awareness in these matters.
Paper Submission and Review Process
The research paper presentations focus on involving students and on encouraging the publication of high-quality, thorough research papers by students and young researchers. To this end, the school will have the following process for submissions:
- Submit an extended abstract of at least 2 and at most 4 pages in Springer LNCS style. From these submissions, the PC chairs select papers within the scope of this call for presentation at the Summer School.
- A full length submission (up to 16 pages), also in Springer LNCS format, is required to be submitted before the Summer School by applicants whose abstract has been accepted. The full-length paper will be shared with the other participants of the Summer School to prepare for the presentations.
- At the Summer School, each author will give a presentation followed by a discussion.
- After the Summer School, authors are invited to submit to the proceedings (again 16 pages LNCS). They are expected to consider the comments and discussions from the Summer School.
- The Programme Committee will review these submissions. Based on these reviews, papers might be accepted, conditionally accepted, or rejected.
- Accepted and (after satisfactory revision) conditionally accepted papers will be included in the Summer School’s proceedings, which will be published by Springer.
Submissions need to be in English language, and must be submitted electronically using the following Easychair link: Paper submission is now closed!
Proposals for Workshops and Tutorials
A workshop is an interactive session scheduled for one or two hours and focuses on involving students in discussion. In it, participants jointly work on a topic or project related to the Summer School theme. Workshop activities are summarized in short papers that recapitulate the outcome and the kinds of discussion raised in the Summer School for inclusion in the proceedings. Proposals for workshops should contain a 2-page statement presenting the topic and summarising the planned activity and the expected contributions from the audience members, e.g., responding to a questionnaire or conducting a small experiment. Proposers should indicate whether any special equipment is needed for the workshop, such as audio-visual systems or computational equipment and support.
Tutorials are one or two-hour-long presentations. They should deal with topics that interest the interdisciplinary audience in the Summer School. Tutorials should provide knowledge on theoretical, empirical, methodological, practical, or other aspects relevant to the Summer School. Tutorial Proposals should contain a 2-page summary and state the level and background required for audience members to follow the tutorial.
Workshop and tutorial proposals need to be in English language, and must be submitted electronically using the following Easychair link: Workshop submission is now closed!
Possible Topics
(can include, but are not limited to)
- Technical and Organisational Measures, Methods, and Tools for Privacy and Data Protection that address:
- Transparency and information provision to data subjects: Addressing the entire lifecycle of generative AI systems, from data collection (including unstructured data scraped from the Web) to secondary uses such as improving models from the contents of user prompts. This includes developing tools to detect unlawful use of personal data by generative AI systems.
- Intervenability and control over personal data: Focusing on mechanisms within generative AI systems, such as machine un-learning, to support deleting personal data from existing models.
- Unlinkability and anonymization: Ensuring the anonymization of personal data during the training and fine-tuning of models to prevent identification.
- Confidentiality in generative AI tools: Exploring local training, federated learning, and encrypted processing (e.g., homomorphic encryption) in generative AI systems.
- Accuracy in AI-generated personal data: Investigating approaches like humility rules, external verification for triangulation, human-on-the-loop (HOTL) feedback mechanisms, and self-improvement protocols that include learning from mistakes.
- Integrity of generative models: Focusing on preventing, detecting, and correcting model poisoning and data poisoning.
- Explainability of AI models: Including both external analyses (e.g., probing, counterfactuals) and internal model improvements (e.g., backtracking to identify influential model features, and source provenance in AI responses). This also encompasses detecting and avoiding bias in generated content and decisions.
- Purpose limitation in data processing: Implementing binding policies to ensure data is used solely for its intended purpose in the context of generative AI.
- Evaluation and performance assessment: Assessing generative AI solutions’ adherence to privacy goals.
- Trustworthiness and Privacy by Design: Incorporating trustworthiness and privacy considerations into the development process of generative AI solutions, focusing on system assurance and compliance traceability.
- Law, Regulation and Governance:
- Data Protection and/or privacy implications of generative AI (transparency, lawfulness, special categories of data, (joint)controllers, data subjects’ rights, DPIAs, publicly available personal data, explainability, etc).
- European and other legislation on data and data governance (Data Act, Data Governance Act, Digital Services Act, Digital Markets Act, Artificial Intelligence Act, etc.).
- The interaction of data protection with liability regulation (product liability reform, AI liability proposal) and/or AI (AI Act).
- Socio-legal implications of generative AI for children, workers, disadvantaged groups, companies, public bodies, governments, society, etc.
- Governance institutions and policy processes, and regulatory bodies at different levels (e.g., national. regional, global).
- The role of experts and the general public in shaping regulation and governance.
- Data justice, data fairness and equality.
- Fundamental rights and accountability in technology and data practices.
- Certification and standardisation.
- Landscape of Generative AI compliance with various regulations.
- AI solutions for regulatory compliance, which aid organizations in adhering to privacy regulations.
- Effects and Impacts (negative or positive):
- Discriminatory effects of technology.
- Technology-enabled social profiling and social exclusion.
- Digital divides, digital dividends, data sovereignty.
- Communities, societies, cultures, and technological mediation.
- Data practices, AI, and the Global South.
- Socio-Technical Perspectives:
- Awareness, attitudes, skills, and behavior of citizens and public and private organizations.
- Approaches for diversity, non-discrimination and democratic enhancement.
- Surveillance, surveillance pressures, chilling effects.
- Critical perspectives on data practices.
- Welfare, solidarity, and care.
- Data economy and ecosystems, new business models.
- Trade-offs, tensions and conflicts between participation in digital cultures and privacy aspects.
- Historical development of data practices.
- Training, awareness, and empowerment of end-users, focusing on educating and equipping them to recognize and address privacy issues in AI effectively.
Why should I submit?
Accepted papers will receive thorough discussions during the school and will allow students to publish their papers in the IFIP AICT series by Springer.
All individual members of IFIP member societies (over 40 national IT societies plus ACM and others) plus all members of IFIP Technical Committees and Working Groups are entitled to a discount of at least 10% on all registration fees.
A course certificate for 1,5 ECTS can be granted to students who attend the Summer School and write a short essay on how their research is relevant to or can be inspired by the Summer School sessions. A course certificate for 3 ECTS can be granted to students who attend the Summer School, submit and present an abstract for a research article, and demonstrate that they have addressed the feedback from the Summer School in an extended version or rebuttal.
We encourage submissions from students from emerging economies: applying for support from the IFIP Digital Equity Fund is possible to ease student travel.
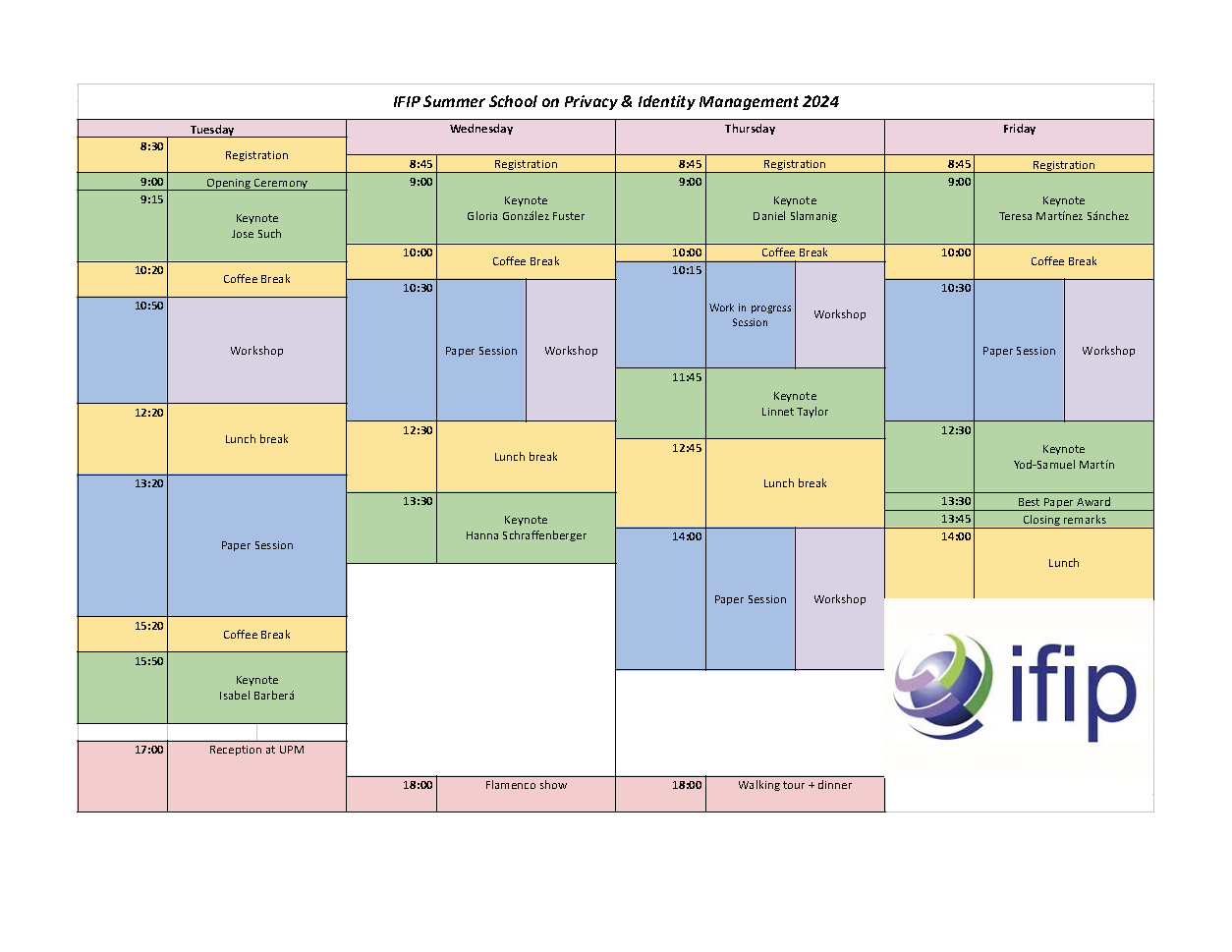
Programme
Overview
Monday, Sep 9th, 2024
19:00 Get-Together
This is an informal Get-Together for those already present. The meeting point will be announced.
Tuesday, Sep 10th, 2024
08:30-09:00 Registration
09:00-09:15 Opening Remarks
(Room: Salón Actos C)
Welcome from the Local Organizers
Welcome from the Steering Committee
09:20-10:20 Keynote: Jose Such
Human-centred AI Security, Ethics and Privacy. This talk will have two main parts: 1) risks in AI systems; 2) AI for online safety. In the first part, I will talk about three risks of using AI: security, privacy, and discrimination. I will show that attacks that can be performed to exploit AI models and attack the systems that use them, that AI-based systems can be privacy-intrusive, and that AI-based systems may have biases that may lead to discriminate against particular types of users (e.g. based on gender/ethnicity). I will then outline our current research and projects on making AI safer. In the second part, I will talk about using AI to help people stay safe online. I will showcase our current research on using AI to study online language, particularly focusing on biased and toxic language and the analysis of echo chambers, and to protect online privacy.
(Room: Salon Actos C, Session Chair: Yod-Samuel Martín)
10:20-10:50 Coffee Break
10:50-12:20 Paper Sessions
| Academic Career Chat: How to navigate a career in research - Tips and tricks, by Silvia De Conca (Room: Salon Actos C) |
12:20-13:20 Lunch Break
13:20-15:20 Paper Sessions
| Track A: Paper Session 3: Subjectivities (Salón Actos C, Session Chair: Silvia De Conca) | ||
| Juliusz Mroziński: Risk Management System in the European Artificial Intelligence Act: Meaning for the Protection of Private and Family Life (Keywords: Fundamental Rights, Digital Human Rights, Right to Privacy and Family Life, European AI Act, Risk Management) | ||
| Atiyeh Sadeghi: Exploring Cultural Values and Privacy Information Concerns: A Model for Immigrant Consumers in Online Markets (Keywords: Privacy information concern, Cultural values, Immigrant, E-commerce use) | ||
| Anastasia Karagianni: Unveiling Shadows: Exploring Privacy, Identity, and Personality Rights in the Age of Sexualised Deepfakes Through Feminist Lenses (Keywords: AI-generated abuse identity, personality rights, privacy sexualised deepfakes) | ||
15:20-15:50 Coffee Break
15:50-16:50 Keynote: Isabel Barberá
GenAI and the Privacy, Agency and Identity Paradox: Redefining Concepts in the Digital Age As Generative AI (GenAI) reshapes our digital landscape, it introduces paradoxes to the worlds of privacy and identity: Can we embrace innovation while avoiding privacy risks? Is GenAI reshaping the way we verify and also perceive our own identities? This keynote will explore how GenAI both empowers and endangers our digital and physical worlds and our understanding of fundamental rights. It will address socio-technical risks as well as the critical role of trust and agency in GenAI systems. The session will challenge traditional data protection paradigms and propose visionary approaches to privacy, agency and identity in the digital age.
(Room: Salón Actos C, Session Chair: Jose M. Del Alamo)
17:00-18:40 Reception at the UPM Telecommunications Engineering School
After the last session, we will have a small reception at the conference site.
In the evening, you are free to mingle and explore the city.
Wednesday, Sep 11th, 2024
09:00-10:00 Keynote: Gloria González Fuster
The future of data and future data laws: Who is to access what The European Union (EU) landscape on the regulation of data has evolved dramatically over the last years. Beyond data-centred instruments such as the Data Act (DA) and the Data Governance Act (DGA), there are new rules on data in acts like the AI Act (AIA), the Digital Services Act (DSA) or the Digital Markets Act (DMA). Data is now more present than ever in EU law, paradoxically coinciding with the proliferation of calls for policy-makers to look beyond data, and/or move on more vigorously into the regulation of networks and infrastructure(s). This talk will look into data, as the persistently privileged object of the EU digital rulebook, highlighting the structuring distinction between personal and non-personal data. It will ask how this distinction (and associated notions such as individual/user control) impact the distribution of access to data, and thus potentially to power and justice, and wonder where this is taking us.
(Room: Salón Actos C, Session Chair: Felix Bieker)
10:00-10:30 Coffee Break
10:30-12:30 Paper Sessions
| Track A: Paper Session 5: Vulnerability & Ethics (Room: Salón Actos C, Session Chair: Gloria González Fuster) | ||
| Saebyoul Yun: A bottom-up movement to develop ethical foundations for generative AI in South Korea: will it simply follow the West or forge its own path? (Keywords: Generative AI and ethics, Ethical guidelines, Emerging movements, Asian Countries) | ||
| Clara Strathmann: A Focus Group Study on Vulnerable Group’s Awareness of Vertical Privacy Online, Protection Measures and the Potential of Offline Analogies (Keywords: vulnerable groups, vertical privacy, visceral notice, inclusion, focus groups) | ||
| Aimen Taimur: Phantoms in the Machine: Examining Legal Ramifications of Large Language Model Hallucinations on Human Opinion Formation (Keywords: Fundamental rights, Cognitive liberty, Generative AI, LLM Hallucinations) | ||
| Track B: Workshop: Liability in the Age of AI: An Interactive Case Study on Data Protection, Discrimination, and Market Integrity, by Marinos Emmanouil Kalpakos and Claudia Negri-Ribalta (Room: B225) | ||
12:30-13:30 Lunch Break
13:30-14:30 Keynote: Hanna Schraffenberger
Digitalization of society: a value-driven design perspective. In this talk, I present past and ongoing projects that address the digitalization of society from a value-driven design perspective. Among other things, I will address issues such as privacy, misinformation, and so-called ‘deceptive design,’ i.e., user interface designs that manipulate users to take actions that might not be in their interest. The primary focus of the talk will be on digital identity wallets and their potential to address societal problems. For instance, I will discuss projects that use identity wallets for email encryption, authenticated video calling, and digital voting, as well as against fake news. We will look at the potential of identity wallets for privacy-friendly disclosure of data but also discuss potential risks - e.g., services tricking users into revealing more data about themselves than is strictly necessary.
(Room: Salón Actos C, Session Chair: Silvia De Conca)
14:30 End of day 2
18:00 Flamenco show
| 17:45 Flamenco Show | Centro Cultural Flamenco de Madrid: Conde de Xiquena 6, 28004 Madrid |
Thursday, Sep 12th, 2024
09:00-10:00 Keynote: Daniel Slamanig
Privacy-Preserving Authentication: Theory vs. Practice With the increasing use of online services, the protection of the privacy of users becomes more and more important. Cryptography offers exciting primitives such as zero-knowledge proofs and advanced signature schemes to realize various forms of so-called anonymous credentials. Such primitives allow to provide a high level of privacy protection. While these primitives are well understood in the research community, unfortunately, they lack widespread adoption. In this talk, we will look at what cryptography can do, some deployment examples, and barriers to adoption, latter using the example of the EU Digital Identity Wallet (EUDIW).
(Room: Salón de Actos C, Session Chair: Ina Schiering)
10:00-10:15 Coffee Break
10:15-11:45 Paper Sessions
| Track A: Work-in-progress session. Please write your name and topic in the list. (Room: Salon Actos C, Session Chair: Felix Bieker) | ||
| Track B: Workshop: CyberSecPro approach to training in Cybersecurity (https://www.cybersecpro-project.eu), by Kai Rannenberg (Room: B225) |
11:45-12:45 Keynote: Linnet Taylor
The global politics of identification ID is political. Identification used to mean primarily the dialogue between citizens and government for administrative purposes, but today ID systems do much more than this. They create marketing opportunities for industry; they shape access to public services; they act as fields of testing and experimentation for financial and security technologies and their governance; they articulate cooperation between governments worldwide around bordering and migration control; they enable law enforcement cooperation nationally and internationally, and much more. In particular, they create fields where security bodies interact and cooperate with civil authorities. This talk will provide a perspective on how these different functions interact in ID systems worldwide, and the interests that are served by these interactions.
(Room: Salón de Actos C, Session Chair: Silvia De Conca)
12:45-14:00 Lunch Break
14:00-16:00 Paper Sessions
| Track A: Paper Session 6: Surveillance (Room: Salón Actos C, Session Chair: Felix Bieker) | ||
| Jorge Constantino Torres: Accounting for data and AI in intelligence and secret services (Keywords: Accountability, data, privacy, generative AI, duty of care in intelligence and security sectors) | ||
| Nils Victor Langensteiner: Pornography Platforms versus Regulators: A comparative overview of the age verification saga (Keywords: youth protection, age verification, online enforcement, pornography) | ||
| Georgios Bouchagiar: Human Rights and Human Duties in the Age of Artificial Intelligence (Keywords: Human rights, Human duties, Artificial Intelligence, Anthropocene) | ||
| Track B: Workshop: Trust data and identity sharing, by Francisco Casino Cembellín and David Arroyo (Room: B225) | ||
16:00 End of day 3
18:00 Walking tour and conference dinner
| 17:50 Guided Walking Tour | Meeting point: Plaza de Oriente (Felipe IV Statue) |
| 20:20 Social Dinner | Restaurante La Catedral: Carrera de San Jerónimo 16, 28014 Madrid |
Friday, Sep 13th, 2024
09:00-10:00 Keynote: Teresa Martínez Sánchez
The role of data protection authorities In an increasingly digital society, where the volume of available data and the technology to exploit it grow at an unprecedented rate, protecting individuals’ rights is intrinsically linked to the protection of their personal data. This talk explores the necessity of effective personal data protection as a crucial first step in safeguarding other fundamental rights and freedoms. Real-life examples are employed to highlight the importance of data protection and the role of data protection authorities in both overseeing the enforcement of these rights and promoting the development of technology designed to protect individuals’ fundamental rights and freedoms. Achieving this requires innovative technological solutions that can adapt to the constant evolution of these technologies.
(Room: Salón de Actos C, Session Chair: Felix Bieker)
10:00-10:30 Coffee Break
10:30-12:30 Paper Sessions
| Track A: Paper Session: Methods & Models (Room: Salón Actos C, Session Chair: Kai Rannenberg) | ||
| Knut Haufe: Generic Process Reference Model for Management Systems (Keywords: management, management systems, process reference models) | ||
| Job Doesburg, Pascal van Gastel, Bernard van Gastel and Erik Poll: A Systematic Method to Design for Privacy & Security in Complex Systems (Keywords: design method, stakeholders, security by design, privacy by design) | ||
| Meem Arafat Manab: TWIG: Two-Step Image Generation using Segmentation Masks as an Intermediary in Diffusion Models to Prevent Copying from the Source (Keywords: Generative Artificial Intelligence, Privacy-Preserving AI, Image Denoising, Diffusion Model) | ||
| Track B: Workshop: DAS – A Digital Adaptation Strategy to jointly shape a post-AI world, by Benjamin Burde and Anna Czeschik (Room: B225) | ||
12:30-13:30 Keynote: Yod-Samuel Martín
Title: Standardizing privacy and data protection for GenAI
(Room: Salón Actos C, Session Chair: Jose M. Del Alamo)
13:30-13:45 Best Student Presentation Award
13:45-14:00 Closing remarks
14:00 Lunch and End of IFIP Summer School 2024
Committee
Programme Chairs
Felix Bieker (ULD)
Silvia De Conca (Vrije Universiteit Amsterdam)
Yod-Samuel Martín (Universidad Politécnica de Madrid)
General Chair
Jose M. Del Alamo (Universidad Politécnica de Madrid)
Steering Committee
Simone Fischer-Hübner (Karlstad University)
Michael Friedewald (Fraunhofer ISI)
Marit Hansen (ULD)
Eleni Kosta (Tilburg University)
Stephan Krenn (AIT Austrian Institute of Technology)
Charles Raab (University of Edinburgh)
Kai Rannenberg (Goethe University Frankfurt)
Ina Schiering (Ostfalia University of Applied Sciences)
Stefan Schiffner (BHH Hamburg)
Diane Whitehouse (EHTEL)
Programme Committee
Florian Adamsky (Hof University of Applied Sciences)
Ala Sarah Alaqra (Karlstad University)
Claudio Ardagna (Università degli Studi di Milano)
David Arroyo (CSIC)
Isabel Barberá (Rhite)
Tanja Böhm (Ostfalia University of Applied Sciences)
Vanessa Bracamonte (KDDI Research, Inc.)
Sebastien Canard (Orange Labs)
Laura Drechsler (KU Leuven)
Prokopios Drogkaris (ENISA)
Michael Friedewald (Fraunhofer)
Nils Gruscka (University of Oslo)
Marit Hansen (ULD)
Meiko Jensen (Karlstad University)
Stefan Katzenbeisser (University of Passau)
Os Keyes (University of Washington)
Agnieszka Kitkowska (Karlstad Univeristy)
Stephan Krenn (AIT Austrian Institute of Technology GmbH)
Konstantinos Limniotis (Hellenic Data Protection Authority)
Zoltan Mann (University of Amsterdam)
Joachim Meyer (Tel Aviv University)
Victor Morel (Chalmers University of Technology)
Frank Pallas (TU Berlin)
Sebastian Pape (Continental Automotive Technologies GmbH)
Davy Preuveneers (imec-DistriNet, KU Leuven)
Arnold Roosendaal (Privacy Company)
Ina Schiering (Ostfalia University of Applied Sciences)
Stefan Schiffner (BHH Hamburg)
Yefim Shulman (Tel Aviv University)
Stefan Strauss (Austrian Academy of Sciences, Institute of Technology Assessment (ITA))
Venue

Summer School Location
The IFIP summer school on privacy and identity management will be located at the
ETSI Telecomunicación, Universidad Politécnica de Madrid.
The address is
Avda. Complutense 30, 28040 Madrid
(see Google Maps)
You can easily reach the building by metro (6-Line) via the station “Ciudad Universitaria”. Details can be found here…
Accommodation
Participants are responsible for securing their own accommodation, as the organizers of the Summer School do not have any agreements with specific hotels or specific recommendations to provide. However, below you will find a list of hotels usually recommended by our host institution (UPM), relatively close to the premises where the Summer School will be held.
- EXE Moncloa C/ Arcipreste de Hita, 10. Madrid +34 917 45 92 99 exehotels.com
- AC Los Vascos C/ Los Vascos, 27. Madrid +34 915 98 62 20 marriot.com
- Hotel Princesa Plaza Madrid C/ Serrano Jover, 3. Madrid +34 915 42 21 00 princesaplaza.com
- Hotel Indigo Princesa C/ Marqués de Urquijo, 4. Madrid +34 915 48 19 00 ihg.com
Green areas surround ETSIT-UPM, and no hotels are within walking distance (all these are more than 30 minutes away on foot). However, ETSIT-UPM can be accessed from these hotels via public transportation. There are direct frequent buses from the first three hotels on the list, and the last two are connected via Metro (2 stops) plus bus (or a 15-minute walk). Additionally, they are conveniently located near a Metro station, making it easy to reach downtown Madrid in just a few stops.
Sponsors