Archive - 20th IFIP Summer School on Privacy and Identity Management 2025
Proceedings
The proceedings are expected to appear in spring 2026.
Call For Papers
Privacy and Data Protection in a Rapidly Changing World
The world as we know it is rapidly changing. Established international agreements and alliances unravel. The principles of liberal democracy are questioned by parts of the population in democratic countries. Large corporations accumulate and use vast amounts of data with little or no legal restrictions, and they are gaining significant political influence. Accepted truths about computers and specifically AI become irrelevant in months. How do these developments affect individuals’ privacy and data protection? Which existing principles remain relevant? Which adaptations need to be made? Which new approaches should be developed?
The 20th IFIP Summer School on Privacy and Identity Management aims to facilitate the exchange of knowledge and insights from the multiple disciplines that deal with privacy, data protection, and identity management. We invite papers that present relevant research in computer science, the law, the social sciences, or other relevant fields for presentation at the summer school and possible inclusion in the proceedings that will be published by Springer.
About the Summer School
The IFIP Summer School on Privacy and Identity Management aims to create a platform for spreading awareness and facilitating interactions and knowledge exchanges around old and new issues by taking a holistic approach to society and technology. We support interdisciplinary research exchange and foster discussions through keynote lectures, tutorials, and workshops. Participants will benefit from presenting their research and receiving meaningful feedback. The IFIP Summer School culminates in the publication of selected papers by the participants as an edited volume published by Springer.
We welcome contributions addressing these issues from any of the following perspectives (and especially the interdisciplinary combination of more than one): sociological, legal, technical, ethical, political, surveillance, intersectional, anthropological, economic, historical, media & communication, regulatory, philosophical, critical, disabilities, and psychological studies in the areas of privacy, data protection, and identity management.
The IFIP Summer School encourages not only interdisciplinarity but also broader diversity. It particularly welcomes submissions on how to foster gender and cultural balance in privacy and identity research and policy, and notably, tutorials and workshops about how to raise awareness in these matters.
Submission and Review Process
Abstracts will undergo a lightweight review process before being invited for a presentation at the conference. Full versions of the submissions, incorporating also feedback received during the summer school, will then be comprehensively reviewed after the conference.
Submissions must be made via the Easychair conference management system.
Details on the review process and the submission link can be found below.
Paper Submission and Review Process
The research paper presentations focus on involving students and on encouraging the publication of high-quality, thorough research papers by students and young researchers. To this end, the school will have the following process for submissions:
- Submit an extended abstract of at least 2 and at most 4 pages in Springer LNCS style. From these submissions, the PC chairs select papers within the scope of this call for presentation at the Summer School.
- A full length submission (up to 16 pages), also in Springer LNCS format, is required to be submitted before the Summer School by applicants whose abstract has been accepted. The full-length paper will be shared with the other participants of the Summer School to prepare for the presentations.
- At the Summer School, each author will give a presentation followed by a discussion.
- After the Summer School, authors are invited to submit to the proceedings (again 16 pages LNCS). They are expected to consider the comments and discussions from the Summer School.
- The Programme Committee will review these submissions. Based on these reviews, papers might be accepted, conditionally accepted, or rejected.
- Accepted and (after satisfactory revision) conditionally accepted papers will be included in the Summer School’s proceedings, which will be published by Springer.
Submissions have to be in English and must be submitted using the following link: link no longer available
Instructions for Workshop/Tutorial Proposals
- Workshop and tutorial proposals must be up to 2 pages and follow the Springer LNCS style. They must include a description of the topic, the expected participants, the types of activities to be carried out, the expected duration, and what support (facilities, infrastructure, etc.) might be needed from the Summer School.
- The title of the submission must start with “WORKSHOP: “ or “TUTORIAL: “, respectively.
Submissions have to be in English and must be submitted using the following link: link no longer available
Possible Topics
Topics of interest include, but are not limited to:
- Technical and Organisational Measures, Methods, and Tools for Privacy and Data Protection that address:
- Transparency and information provision to data subjects: Addressing the entire lifecycle of generative AI systems, from data collection (including unstructured data scraped from the Web) to secondary uses such as improving models from the contents of user prompts. This includes developing tools to detect unlawful use of personal data by generative AI systems.
- Intervenability and control over personal data: Focusing on mechanisms within generative AI systems, such as machine un-learning, to support deleting personal data from existing models.
- Unlinkability and anonymization: Ensuring the anonymization of personal data during the training and fine-tuning of models to prevent identification.
- Confidentiality in generative AI tools: Exploring local training, federated learning, and encrypted processing (e.g., homomorphic encryption) in generative AI systems.
- Accuracy in AI-generated personal data: Investigating approaches like humility rules, external verification for triangulation, human-on-the-loop (HOTL) feedback mechanisms, and self-improvement protocols that include learning from mistakes.
- Integrity of generative models: Focusing on preventing, detecting, and correcting model poisoning and data poisoning.
- Explainability of AI models: Including both external analyses (e.g., probing, counterfactuals) and internal model improvements (e.g., backtracking to identify influential model features, and source provenance in AI responses). This also encompasses detecting and avoiding bias in generated content and decisions.
- Purpose limitation in data processing: Implementing binding policies to ensure data is used solely for its intended purpose in the context of generative AI.
- Evaluation and performance assessment: Assessing generative AI solutions’ adherence to privacy goals.
- Trustworthiness and Privacy by Design: Incorporating trustworthiness and privacy considerations into the development process of generative AI solutions, focusing on system assurance and compliance traceability.
- Law, Regulation and Governance:
- Data Protection and/or privacy implications of recent political, legal and technological developments (transparency, lawfulness, special categories of data, (joint)controllers, data subjects’ rights, DPIAs, publicly available personal data, explainability, etc).
- European and other legislation on data and data governance (Data Act, Data Governance Act, Digital Services Act, Digital Markets Act, Artificial Intelligence Act, etc.).
- The interaction of data protection with liability regulation (product liability reform) and/or AI (AI Act).
- Socio-legal implications for children, workers, disadvantaged groups, companies, public bodies, governments, society, etc.
- Governance institutions and policy processes, and regulatory bodies at different levels (e.g., national. regional, global).
- The role of experts and the general public in shaping regulation and governance.
- Data justice, data fairness and equality.
- Fundamental rights and accountability in technology and data practices.
- Certification and standardisation.
- AI solutions for regulatory compliance, which aid organizations in adhering to privacy regulations.
- Effects and Impacts (negative or positive):
- Discriminatory effects of technology.
- Technology-enabled social profiling and social exclusion.
- Digital divides, digital dividends, data sovereignty.
- Communities, societies, cultures, and technological mediation.
- Data practices, AI, and the Global South.
- Socio-Technical Perspectives:
- Awareness, attitudes, skills, and behavior of citizens and public and private organizations.
- Approaches for diversity, non-discrimination and democratic enhancement.
- Surveillance, surveillance pressures, chilling effects.
- Critical perspectives on data practices.
- Welfare, solidarity, and care.
- Data economy and ecosystems, new business models.
- Trade-offs, tensions and conflicts between participation in digital cultures and privacy aspects.
- Historical development of data practices.
- Training, awareness, and empowerment of end-users, focusing on educating and equipping them to recognize and address privacy issues in AI effectively.
Why should I submit?
Accepted papers will receive thorough discussions during the school and will allow students to publish their papers in the IFIP AICT series by Springer.
All individual members of IFIP member societies (over 40 national IT societies plus ACM and others) plus all members of IFIP Technical Committees and Working Groups are entitled to a discount of at least 10% on all registration fees.
A course certificate for 1,5 ECTS can be granted to students who attend the Summer School and write a short essay on how their research is relevant to or can be inspired by the Summer School sessions. A course certificate for 3 ECTS can be granted to students who attend the Summer School, submit and present an abstract for a research article, and demonstrate that they have addressed the feedback from the Summer School in an extended version or rebuttal.
We encourage submissions from students from emerging economies: applying for support from the IFIP Digital Equity Fund is possible to ease student travel.
Call for Workshops and Tutorials Proposals
A workshop is an interactive session scheduled for one or two hours and focuses on involving students in discussion. In it, participants jointly work on a topic or project related to the Summer School theme. Workshop activities are summarized in short papers that recapitulate the outcome and the kinds of discussion raised in the Summer School for inclusion in the proceedings. Proposals for workshops should contain a 2-page statement presenting the topic and summarising the planned activity and the expected contributions from the audience members, e.g., responding to a questionnaire or conducting a small experiment. Proposers should indicate whether any special equipment is needed for the workshop, such as audio-visual systems or computational equipment and support.
Tutorials are one or two-hour-long presentations. They should deal with topics that interest the interdisciplinary audience in the Summer School. Tutorials should provide knowledge on theoretical, empirical, methodological, practical, or other aspects relevant to the Summer School. Tutorial Proposals should contain a 2-page summary and state the level and background required for audience members to follow the tutorial.
Workshop and tutorial proposals need to be in English language, and must be submitted electronically.
Important Dates
All dates are AoE (anywhere on earth).
| Event | Deadline |
|---|---|
| Abstracts Deadline: | 26.05.2025 |
| Workshops and Tutorials Proposal Deadline: | 26.05.2025 |
| Acceptance Decision: | 02.06.2025 |
| Early bird registration Deadline: | 22.07.2025 |
| Full Paper Deadline: | 05.08.2025 |
| Summer School: | 19.-22.08.2025 |
| Revised Full Paper Deadline: | 30.09.2025 |
| Full Paper Feedback: | 15.11.2025 |
| Camera Ready Deadline: | 15.12.2025 |
Program
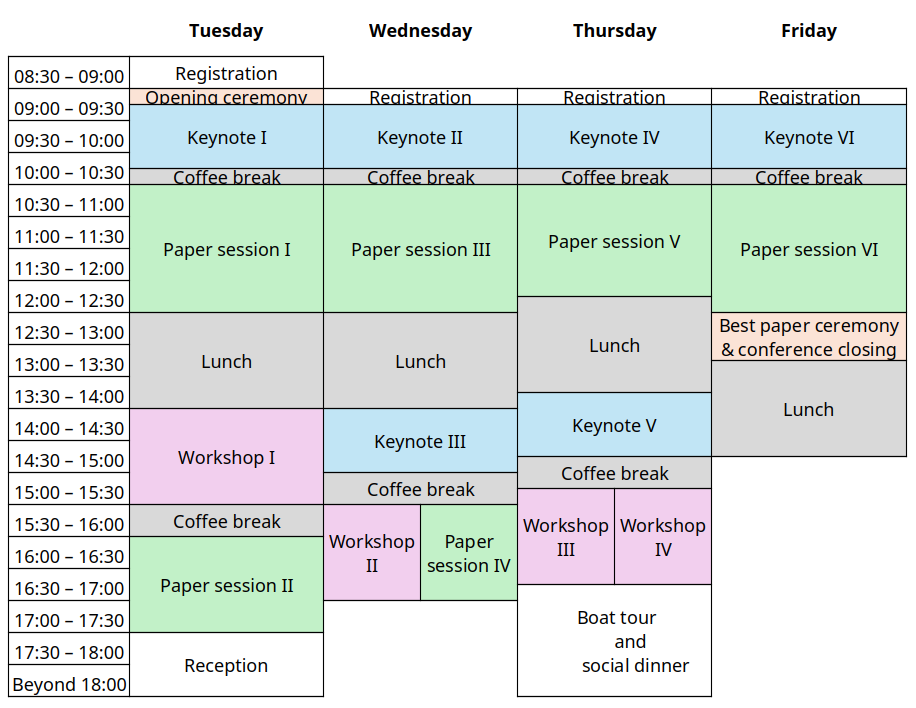
Program at a Glance
Detailed Program
Day 1 :: Tuesday, August 19, 2025
8:30 – 9:00: Registration
9:00 – 9:15: Opening remarks
9:15 – 10:15: Keynote I
Nicolás E. Díaz Ferreyra: Privacy as Practice: Perspectives from Users and Developer-Centred Research
10:15 – 10:30: Coffee break
10:30 – 12:30: Paper session I
- Laura Macpherson: Sovereignty.exe: The EU’s Digital Dilemma
- Sargam Gupta and Vicenç Torra: Fed-PUP : Federated Learning with Personalized User Privacy
- Giovanni Chieco: Digital Sovereignty in the Age of Big Tech: A Possible Pathway for the European Union Beyond Regulatory Activism?
- Derya Sözen Esen: Toward a Unified Meta-Framework for AI Auditing: A PRISMA Scoping Review of Post-2023 Governance Frameworks and Blind Spots
12:30 – 14:00: Lunch break
14:00 – 15:30: Workshops
- Workshop I: Ramona Adair, Ina Schiering and Tom Lorenz: Privacy Awareness Cards
15:30 – 16:00: Coffee break
16:00 – 17:30: Paper session II
- Ricardo Bochnia, Eric Biele, Daniel Richter and Jürgen Anke: Onboarding Processes of Trusted Actors in Self-Sovereign Identity Ecosystems
- Karl Koch: QœSign: Qualified Collaborative eSignatures
- Jakob Heher, Emanuel Pichler and Stefan More: Genuine PDF Forgeries
17:30: Welcome reception
Day 2 :: Wednesday, August 20, 2025
9:00 – 9:15: Registration
9:15 – 10:15: Keynote II
Agnieszka Kitkowska: What We Assume, What We Miss: Rethinking How We Understand and Design for Privacy
10:15 – 10:30: Coffee break
10:30 – 12:30: Paper session III
- Christina Karakosta, Lian Alhedaithy and William J. Knottenbelt: Scalable Privacy-Preserving Iris Recognition: Challenges and Outlook
- Halid Kayhan: Post-hoc Explainability in AI-enabled Clinical Decision Support Systems: Enhancing Shared Decision-Making or Raising New Risks
- Meem Arafat Manab and Victor Gonzalez Castro: Private Information is Language Knowledge: GDPR Compliance, Privacy Rights, and the Catastrophe of Systematic Linguistic Degradation
- Jan Lühr, Foivos Ioannis Michelinakis and Tarik Cicic: Private Microsegmentation for Smart Homes
12:30 – 14:00: Lunch break
14:00 – 15:00: Keynote III
Andrej Savin: Navigating AI and Data Privacy: Clarifying the Relationship between the AI Act and GDPR
15:00 – 15:30: Coffee break
15:30 – 17:00: Parallel Session
- Paper session IV
Session Chair: Stefan Schiffner
- Frederick Gaß: Tensions between the Data Act and the GDPR within the Use of IoT Products
- Nicola Leschke: Engineering Personal Data Access: A Procedural Perspective on Challenges and Solutions
- Yuwen Zhang and Michael Friedewald: Theory and Practice of Data Portability A Systematic Literature Review
- Workshop II: Gurvirender Tejay and Umit Cali: Connected Vehicles and Digital Privacy: An Applied Workshop using IEEE Digital Privacy Model
Day 3 :: Thursday, August 21, 2025
9:00 – 9:15: Registration
9:15 – 10:15: Keynote IV
Katherine Quezada Tavárez: Building Bridges in Privacy and Data Protection: A Practitioner’s Tale of Interdisciplinary Work
10:15 – 10:30: Coffee break
10:30 – 12:15: Paper session V
- Maria Skwarcan: Pay or Consent Under the DMA: Genuine Progress or Illusory Victory Against Data Commodification?
- Lelia Hanslik, Stefan Ullrich and Bettina Berendt: From Advertised Features to Third Party Privacy Impact Assessments
- Nikolas Wintering and Nils Aschenbruck: Towards a Privacy-aware Role-based Network Intrusion Detection System
12:15 – 13:45: Lunch break
13:45 – 14:45: Keynote V
Paul Stankovski Wagner: Digitalization & PAPR: Publicly Auditable Privacy Revocation for Anonymous Credentials
14:45 – 15:15: Coffee break
15:15 – 16:45: Workshops
- Workshop III: Michael Friedewald, Marc Steen and Greta Runge: Citizen Engagement in Cybersecurity Research
- Workshop IV: Kai Rannenberg et al.: The CyberSecPro approach to training in Cybersecurity and its relation to Privacy and Identity Management
after the end of the last session: Boats tour and social dinner
Day 4 :: Friday, August 22, 2025
9:00 – 9:15: Registration
9:15 – 10:15: Keynote VI
Anja Moller Pedersen: Facial Recognition Technology for Law Enforcement Purposes in Denmark: Parliamentary Support Without Democratic Legitimacy
10:15 – 10:30: Coffee break
10:30 – 12:30: Paper session VI
- Isabela Maria Rosal: Private actors processing data for archival purposes: a fight for public interest
- Neshe Tuna and Ala Sarah Alaqra: Bridging the Cybersecurity Gap: Agile Approaches in Multi-stakeholder Collaboration in the Public Sector
- Metehan Gelgi, Maria Papaioannou and Nicola Dragoni: Toward Cost-Effective Secure Multi-Site Connectivity: Evaluating NSA’s CSfC-Compliant Open-Source and Commercial Solutions
- Jed Boufaied and Vicenç Torra: On Explanations And Privacy: An AIT Approach
12:30 – 13:00: Best paper ceremony & closing remarks
13:00 – 14:00: Lunch break
Keynote Speakers
We are grateful to following keynote speakers for their contributions to the 20th IFIP Summer School on Privacy and Identity Management (listed in alphabetical order).
🇩🇪 Hamburg University of Technology, Institute of Software Security
Title: Privacy as Practice: Perspectives from Users and Developer-Centred Research
Abstract: Information disclosure is essential to many digital services, ranging from social networks to critical domains like healthcare and finance. Yet privacy decisions are often based on spurious or incomplete assessments of risk, which often translate into unwanted incidents for end users. This challenge has been addressed from multiple angles, including psychology, information systems, and law. Furthermore, prior work has elaborated extensively on preventative technologies that aim at supporting users’ privacy choices through behavioural interventions or “nudges”. However, much less attention has been paid to privacy decision-making within software development processes. Particularly, to the personal and project-sensitive information exchanged by practitioners as they deploy software-intensive systems, and the associated risks. In this talk, I will share some lessons I have learned while investigating self-disclosure practices in social networks and elaborate on how they can help us shape a research agenda for privacy in software development environments. I will also review the current state of the art on privacy engineering methods and discuss prospective research directions in the area of privacy ‘as code’.
🇸🇪 Jönköping University, Department of Computer Science and Informatics , School of Engineering
Title: What We Assume, What We Miss: Rethinking How We Understand and Design for Privacy
Abstract: Designing technical solutions that aim to help people make more informed decisions about their privacy might be challenging. To make such tools usable and relevant to individuals, one must understand factors that affect people's behavior. Privacy research in the past has revealed many of these factors, such as privacy concerns, personality characteristics, or previous experiences. However, when designing for privacy, certain assumptions are often made, such as stereotyping or generalizing about the privacy consequences. In this talk, we will discuss how such approaches might be misleading and how modern norm-critical approaches, such as intersectionality, can help gain a deeper understanding of the privacy-related decisions made by various individuals or groups.
🇩🇰 Danish Institute for Human Rights & University of Copenhagen, Faculty of Law
Title: Introducing Facial Recognition Technology for Law Enforcement Purposes in Denmark: Parliamentary Support Without Democratic Legitimacy
Abstract: In 2024, the Danish Parliament gave its support to the police to start using facial recognition technology (FRT) for law enforcement purposes. However, the exact scope and conditions for use remain unknown to the public as the use of FRT has no distinct legal basis but is based on the general competences of the police to investigate criminal activities and process personal data. The keynote explores this interference with the fundamental rights in Art 8 ECHR and Arts 7 and 8 CFREU against the requirements of lawfulness in Art 8(2) ECHR and ‘strict necessity’ in relation to Art 8 CFREU and discusses more generally the ways in which digital investigative tools are regulated with varying levels of detail and democratic scrutiny.
🇧🇪 UZ Leuven
Title: Building Bridges in Privacy and Data Protection: A Practitioner’s Tale of Interdisciplinary Work
Abstract: How do lawyers, engineers, security professionals, data scientists, ethicists, business leaders, and clinicians actually work together on privacy and data protection? And what happens when they do not? Drawing on an enduring trajectory at the intersection of law, ethics, compliance, research, and technology, this keynote explores the practical realities of a data protection career across academic, corporate, and healthcare settings. It dives into the human complexity of privacy governance, where disciplinary divides, competing priorities, and communication gaps can hinder progress, but also where genuine collaboration can drive meaningful change. Through lived examples and professional insights, the talk reflects on what it takes to build functional, trusted, and resilient data protection cultures in practice.
🇩🇰 Copenhagen Business School, Department of Business Humanities and Law
Title: Navigating AI and Data Privacy: Clarifying the Relationship between the AI Act and GDPR
Abstract: The Artificial Intelligence Act (AI Act) is a comprehensive regulatory framework designed to govern Artificial Intelligence (AI) within the European Union (EU) through risk-based, ex ante horizontal product-safety rules. Artificial Intelligence (AI) systems heavily rely on data sets for training, and these data sets are subject to the General Data Protection Regulation (GDPR) in the extent that they are based on personal data. This interplay between GDPR and the AI Act raises several compliance challenges. This presentation provides an overview of the primary issues pertaining to the relationship between the GDPR and the AI Act. We will delve into matters such as the scope of application, the legal hierarchy, the allocation of responsibility, and the legal foundations of compliance. The overarching concept is that adhering to GDPR compliance may often prove to be the more onerous of the two regulatory frameworks.
🇸🇪 Lund University, Department of Electrical and Information Technology
Title: Digitalization & PAPR: Publicly Auditable Privacy Revocation for Anonymous Credentials
Abstract: Digitalization is a popular word nowadays, but what is digitalization really, is it just fluff or is it concretely useful? Digitalization can help us to build better systems, technical systems with new properties, but to see how and why, we need to first talk about some basics. An engineering interpretation of digitalization, and how it is changing engineering education at Lund University. PAPR is a technical system that provides auditability to privacy revocation systems. Simply explained, think of a centralized system in which the system owner holds all user data and can apply mass surveillance at will. With PAPR techniques, we decentralize user data to build a system that cannot be used for mass surveillance without the users knowing about it. That is, if the system is mis-used, we (users) will know about it. This brings a whole different level of (potential) public trust into a proprietary system, letting the users audit the system they are using. A small step towards achieving and maintaining privacy and data protection in a rapidly changing world, aimer at higher objectives in future technical systems. The PAPR paper was published at CT-RSA in 2023.
Best Presentation Award
Two best presentation awards were awarded at this year’s summer school:
- Nicola Leschke for her paper “Engineering Personal Data Access: A Procedural Perspective on Challenges and Solutions”
- Maria Skwarcan for her paper “Pay or Consent Under the DMA: Genuine Progress or Illusory Victory Against Data Commodification?”
We congratulate Nicola and Maria!
Committee
Programme Chairs
- Laura Drechsler (🇧🇪 KU Leuven)
- Yod Samuel Martin Garcia (🇪🇸 Universidad Politécnica de Madrid)
- Joachim Meyer (🇮🇱 Tel Aviv University)
General Chairs
- Lejla Islami (🇩🇰 Technical University of Denmark)
- Stephan Krenn (🇦🇹 AIT Austrian Institute of Technology)
Steering Committee
- Simone Fischer-Hübner (🇸🇪 Karlstad University) – Chair
- Felix Bieker (🇩🇪 ULD)
- Silvia De Conca (🇳🇱 Vrije Universiteit Amsterdam)
- Michael Friedewald (🇩🇪 Fraunhofer ISI)
- Marit Hansen (🇩🇪 ULD)
- Eleni Kosta (🇳🇱 Tilburg University)
- Stephan Krenn (🇦🇹 AIT Austrian Institute of Technology)
- Charles Raab (🇬🇧 University of Edinburgh)
- Kai Rannenberg (🇩🇪 Goethe University Frankfurt)
- Ina Schiering (🇩🇪 Ostfalia University of Applied Sciences)
- Stefan Schiffner (🇩🇪 BHH Hamburg)
- Diane Whitehouse (🇧🇪 EHTEL)
Programme Committee
- Felix Bieker (🇩🇪 ULD)
- Simone Fischer-Hübner (🇸🇪 Karlstad University)
- Michael Friedewald (🇩🇪 Fraunhofer ISI)
- Jesús García-Rodríguez (🇪🇸 University of Murcia)
- Nils Gruschka (🇳🇴 University of Oslo)
- Tejay Gurvirender (🇺🇸 Hofstra University)
- Stefan Katzenbeisser (🇩🇪 University of Passau)
- Konstantinos Limniotis (🇬🇷 National and Kapodistrian University of Athens)
- Stefan More (🇦🇹 Graz University of Technology)
- Davy Preuveneers (🇧🇪 DistriNet, KU Leuven)
- Kai Rannenberg (🇩🇪 Goethe University Frankfurt)
- Arnold Roosendaal (🇳🇱 Privacy Company)
- Ina Schiering (🇩🇪 Ostfalia University of Applied Sciences)
- Stefan Schiffner (🇩🇪 BHH Hamburg)
- Yefim Shulman (🇳🇱 Erasmus University Rotterdam)
Venue
The summer school will be hosted by the Technical University of Denmark (DTU) in Copenhagen, Denmark. The school will take place in Building 101.
Travel Information
Hotel Recommendations
Participants are responsible for selecting and booking hotels depending on their needs and priorities. However, we provide some suggestions below:
- Hotels near to the university
- Four Points Flex by Sheraton Lyngby, Lundtoftegardsvej 12 Kongens Lyngby
- Hotels in Copenhagen
-
Wakeup Copenhagen**, Carsten Nieburs Gade 11, Copenhagen
-
Comfort Hotel Vesterbro***, Vesterbrogade 23-29, Copenhagen
-
Tivoli Hotel & Congress Center**, Arni Magnussons Gade 2, Copenhagen
-
Travel Information
Copenhagen airport (CPN) is connected by direct flights to many international destinations. However, there are no direction train or bus connections from the airport to DTU.
We recommend the following routes:
- Through Helsingørmotorvejen (The Helsingør Highway)
- Metro - M2 (Direction: Vanløse) to [Nørreport St.]
- Express Bus - 150S (Direction: Kokkedal) / 15E (Direction: Søhuset Forskerparken) to [Rævehøjvej, DTU]
- Through Local S-Train
- Metro - M2 (Direction: Vanløse) to [Nørreport St.]
- S-Train - A (Direction: Hillerød)/E (Direction: Holte) to [Lyngby St.]
- Regional Bus 180/181 (Direction: DTU), 190 (Direction: Holte), Express Bus 300S (Direction: Gl. Holte) / 30E (Direction: DTU) to [DTU (Anker Engelunds Vej)]
Rejsekort (Travel Card)
Rejsekort (Travel Card) is a prepaid card for taking public transportations in Denmark.
You can obtain an anonymous card in convenient stores or at Rejsekort machines. We suggest you buy your Rejsekort already at the airport.
When you are hopping on or off a ride (e.g,. Entering or Leaving Metro), please remember to check yourself in or out accordingly. If you forgot to check yourself out, credit in the card will be deducted with the highest fee of the last route you’ve taken after a day or two. If you forgot to check yourself in and hopping on to a ride, a fine of 750 DKK will be enforced if a ticket inspector reached you.
When checking out, remember to look at how much credit you’ve left on the card. If the credit on the card is less than 60 DKK, you may find yourself unable to check-in on the next ride.
To recharge your card, go to the Rejeskort machine or a Convenient store.
Rejseplanen (Journey Planner)
Rejseplanen (Journey Planner) is a service you can reach through web or app, to search the best combination of public transportations from where you are at to where you would like to go, in Denmark. It is also available as app for Android or iPhone.
Taxi
You can easily catch a taxi near most train stations. If you’re not near a station and need a ride, you’ll need to call a local taxi company. Most drivers accept credit cards, but it’s a good idea to check with the driver before starting your trip.
Misc
- In Denmark, dial ✆112 for emergency services – ambulance, police, or fire department.
- The currency in Denmark is the Danish Krone (DKK), and the exchange rate is approximately 7.46 DKK to 1 EUR (or 100 DKK = 13.41 EUR). (Note: Exchange rates may vary!)
Registration
For each accepted abstract, at least one (co-)author has to attend the summer school and register by the early-bird registration deadline.
Registration fees have to be paid in Danish Krone (DKK). The exchange rate is approximately 1’000 DKK = 134.06 EUR). (Note: Exchange rates may vary!)
| Registration type | Early bird1 | Late registration1 |
|---|---|---|
| Regular registration | 4’400 DKK | 4’900 DKK |
| IFIP Member registration2 | 3’960 DKK | 4’410 DKK |
1 Early bird registration fees apply until July 22.
2 All individual members of IFIP member societies as well as all members of IFIP Technical Committees (TCs) and Working Groups (WGs) are entitled to a discount of 10% on registration fees. To claim the discount, you will need to state which IFIP member society/TC/WG you belong to during the registration process.
Please register under the following link: https://www.conferencemanager.dk/ifipsummerschool2025
Sponsors


Supporters






